Skip ahead
- What is HTTP?
- Advantages of HTTP
- Limitations of HTTP
- What is HTTPS, then?
- How does TLS/SSL encrypt HTTP requests and responses?
- Benefits of HTTPS
- Limitations of HTTPS
- Difference between HTTP and HTTPS
- Looking beyond the differences between HTTP and HTTPS.
- What is SPDY?
- What about HTTP/2?
- What is HTTP/3?
- How to switch from HTTP to HTTPS
- How to choose SSL certificate
- Conclusion
The key difference between HTTPS and HTTP is the presence of encryption. Simply put, HTTPS is HTTP with encryption. The most important difference between these two protocols is that HTTPS uses TLS (SSL certificate) to encrypt normal HTTP requests and responses. So, the HTTPS protocol has become more secure in terms of data storage and transmission than HTTP. How can you distinguish what is the protocol in a URL? It's simple, its address starts with http://, while a website using HTTPS has https://.
If you’ve been wondering about the main differences between the HTTP and HTTPS protocol, we can help. People come to us all the time asking questions like, “What is the protocol in a URL? What does HTTP stand for? What does HTTPS mean? Why use HTTPS? How can I convert HTTP to HTTPS?” Experts in professional seo services from Direct Line Development are here to answer all your questions.

Many people are confused about whether, how, and when to upgrade to HTTPS from HTTP, so if that’s you, you’re definitely not alone. We’ve looked closely at the nuances between the two protocols, HTTP vs HTTPS, so we can help you sort it all out.
Perhaps you’re concerned about HTTPS SEO. Interestingly, both HTTP protocol and HTTPS protocol have had a positive impact on SEO in 2021, a trend that is projected to continue in 2022. So it pays to learn more about them. In this article, we’ll see how all of these protocols stack up:
- HTTP
- HTTPS
- SPDY
- HTTP/2
Let’s start by looking at the advantages and limitations of HTTP and HTTPS in detail.
What is HTTP?
HTTPS stands for Hypertext Transfer Protocol. Add one more letter meaning “secure”, and you get HTTPS. As you likely have noticed, these are typically found at the beginning of website URLs, denoted as http:// and https:// when you enter a website address into the URL bar at the top of your browser. But they are more than simply part of the address. The differences become apparent when you explore the advantages and limitations of each protocol at the highest level and then in greater detail.
What’s the difference between http and www? Web browsers and servers, using the HTTP protocol, indicate that they are part of the World Wide Web (WWW), so http is a part of www.

What is HTTP, without the “S”?
We’ve been entering “HTTP” in the address bar for various websites for a long time, so you may have already recognized the term as Hypertext Transfer Protocol. HTTP represents the international standard for how computer programs essentially talk to one other over a network.
Advantages of HTTP
The primary advantages of HTTP are in its simplicity and ease of use.
- Fewer demands. - HTTP requires lower CPU and memory usage. There are fewer simultaneous connections required in HTTP than in more secure protocols.
- Data pipelining. - HTTP enables requests and responses to be pipelined. Data pipelining is an orderly process allowing multiple instructions to be overlapped and stored by a data processor.
- Less congestion. - HTTP reduces network congestion. This is because it requires fewer TCP connections (TCP stands for TCProtocol, a type of information transmission protocol).
- Speed of requests. - Exchanging signals between computers (known as “handshaking”) happen only during the initial connection. Once the connection is established, subsequent requests can happen without delay.
- Connections. - HTTP won't close a TCP connection. It can report errors without shutting things down, which may be preferred in certain circumstances.
Limitations of HTTP
Despite its ease of use, following are some of the downsides, or limitations, of HTTP. These include insecure connections, rather basic capabilities, and server issues.
- Insecure connections. - HTTP allows point-to-point connection. This is a challenge for keeping a website secure, as information may become disclosed to third parties more easily.
- Basic capabilities. - HTTP is considered to be a bit verbose. It's not optimized for mobile. It doesn't have "push capabilities.” So in these ways, HTTP is seen as a fairly basic protocol.
- Server issues. - The server won't be available if a client closes a connection before all the needed data has been received. No one wants to see server error messages unnecessarily.
What is HTTPS, then?
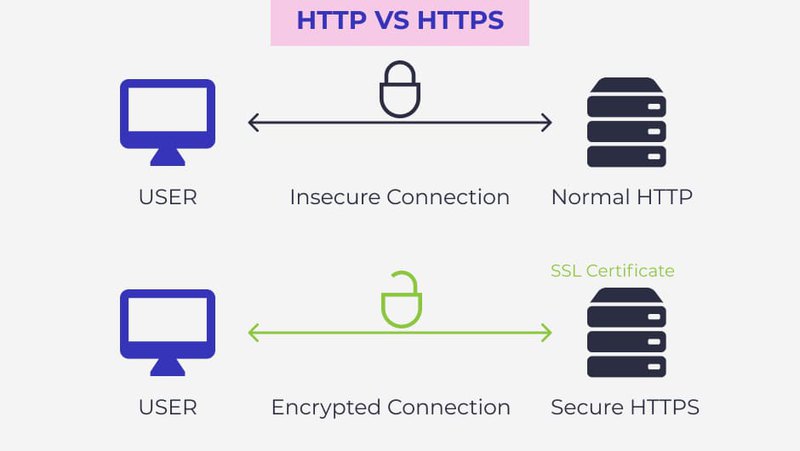
HTTPS was initially developed to keep payment transactions and sensitive corporate data secure. However, in 2016 a group of web developers campaigned to make the protocol more prevalent, helping to ensure greater privacy and data protection all around. The result is that HTTPS has become more commonly used, so we are all seeing the moniker “HTTPS” more often today. Sometimes mistakenly typed into a web browser as “https //” or “https;” HTTPS sites have URLs that are written as https://.
Some people ask us, “What is the difference between SSL and HTTPS?” or “What is HTTPS vs SSL?” The answer is that ssl and https are different entities. HTTPS encrypts the communication protocol using Transport Layer Security (TLS), previously Secure Sockets Layer (SSL). So it may alternately be called "HTTP over TLS," or "HTTP over SSL."
How does TLS/SSL encrypt HTTP requests and responses?
What port is for HTTPS? To encrypt data, TLS uses port 443 with a special technology that includes working with two keys: public and private. The principle of operation is as follows - the public key is transmitted to the client's devices via the server's SSL certificate. When connecting to the server, the two devices involved in the operation use the public and private keys to select new keys (session keys) to encrypt further messages passing from one device to another with HTTP vs HTTPS.
All HTTPS vs HTTP requests and responses to them are encrypted using these session keys, so if a message is intercepted by third parties or devices, when it is opened and decryption is attempted, a random string of characters will be received instead of a coherent, plain text if you use HTTPS.
Some benefits of HTTPS
We’re often asked, “Is https secure?” As its name indicates, the HTTPS protocol is more secure than the original version of HTTP. The HTTPS protocol blocks intermediaries (caches, proxies, etc.) between the client and server. Because the content is encrypted, it prohibits interlopers from interfering with requests and responses. HTTPS websites are generally considered safer than HTTP websites.
- Search engine visibility. - An often overlooked benefit of HTTPS is that it is actually preferred by search engines such as Google.
- Data encryption. -HTTPS encryption prevents hackers from snooping or tampering with your website traffic. Even if a hacker intercepts data between the client and the server, the data will be useless to the hacker because it is encrypted.
- Data protection. - No "cookies" and only very limited data (if any) can be saved on the client system.
- Server authentication. - In the authentication process, servers look at the CA (certificate authority or certification authority) to check such things as the validity of dates, authority, digital signature, and domain name to help protect users from hackers.
- Data validation. -HTTPS also conducts more extensive data validation or “handshaking” for each incident of information exchange, rather than only relying on the initial exchange for validation.
| Protocol | Security | Data | Layer | Certificates |
| HTTP | Unsecured | port 80 | Application layer | No SSL certificates required |
| HTTPS | Secured | port 443 | Transport layer | SSL certificate signed by a CA |
Limitations of HTTPS
The limitations of HTTPS include higher costs, greater potential for error displays, and additional requirements. It also raises concerns about performance, scalability, and evolvability.
- Costs -There's an annual cost to hold the HTTPS certificate. Prices typically vary based on the number of domains or subdomains the certificate will cover. The level of identity verification also affects the price.
- Errors - If the certificate expires (or is not renewed for any reason), the site will display errors. In fact, it may not display anything at all, unless reverted back to HTTP.
- Requirements - Additional computational overhead is required to manage data processing.
- Performance - Generally speaking, HTTPS runs a bit slower than HTTP, so performance can become something to consider.
- Scalability - In a fully secured network, innovations are less likely to be replicated, and less quickly, than in open environments. So scalability is another consideration.
- Less evolvability - Computer scientists like to promote “evolvability,” or an ability to learn, grow, and adapt. Because of their closed nature, more secure networks are less instantly evolvable.
So, that’s an overview of how HTTPS works, as well as HTTP.
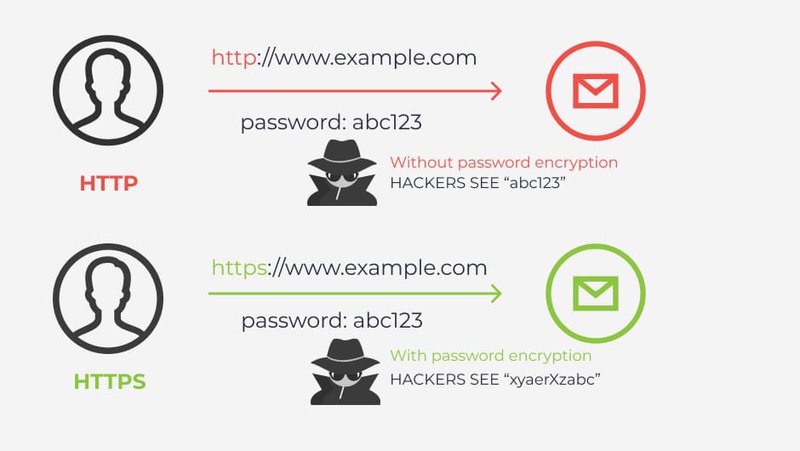
Difference between HTTP and HTTPS
| Protocol | HTTP | HTTPS |
| Security | Unsecured | Secured |
| Data | Port 80 | Port 443 |
| Layer | Application layer | Transport layer |
| Start with | http:// | https:// |
| Certificates | No SSL certificates required | SSL certificate signed by a CA |
| Suitable for | Blogs, forums, educational sites, entertainment and articles. | Payment gateways, shopping websites. |
| Speed | Fast | Slower than HTTP |
| SERP ranking | Don’t improve | Improve |
| Encryption | Don’t use | Use |
Looking beyond the differences between HTTP and HTTPS
When considering the limitations and advantages of HTTP and HTTPS protocols, the reasons for the difference in the level of security become much clearer, don’t they? You can really sense why a business might choose one over the other.
However, there are other protocols we are often asked about as well, including SPDY and HTTP/2. These other popular protocols were developed with speed and convenience in mind.
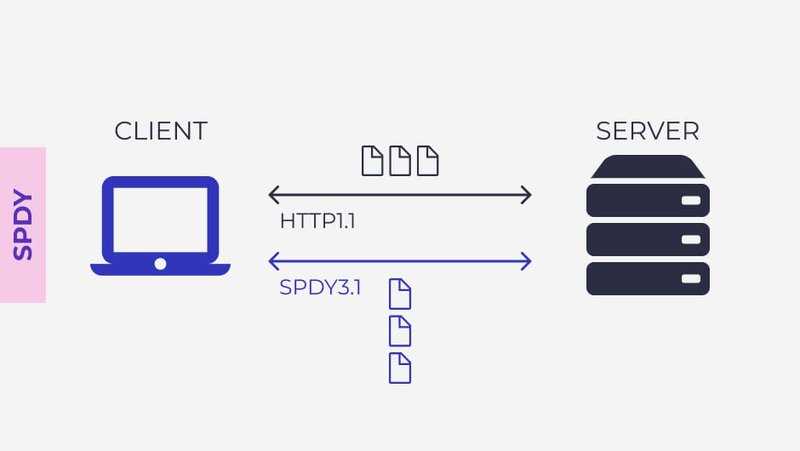
What is SPDY?
SPDY (pronounced "speedy") is Google’s attempt at creating a protocol that helps make the web run faster on HTTP. It was an experimental protocol, also sometimes called "a deprecated open-specification networking protocol."
SPDY was designed to use different types of compression for HTTP headers attached to every request and response in network computing. It uses compression to download text content, improving speed and performance.
What about HTTP/2?
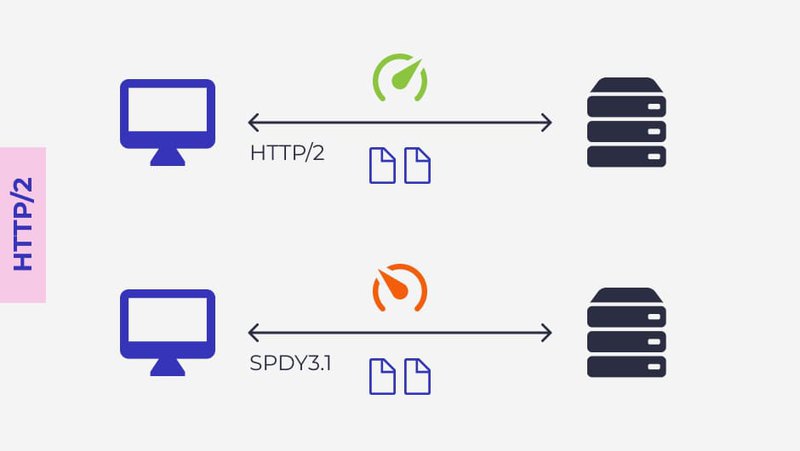
While HTTP/2 is based on the SPDY protocol and also uses compression, HTTP/2 uses an algorithm designed for newer websites. Sites have become quite resource-intensive over time as additional “bells and whistles” have been added. Just think about how dynamic a website’s content is today compared to 10 years ago. A lot has changed.
HTTP/2 has been shown to be consistently even faster than SPDY. Therefore, among these protocols Google has announced in recent years that it is withdrawing support for SPDY in favor of supporting HTTP/2.
HTTP/2 protocols have many advantages over HTTP 1.0. The bottom line is that it’s safe to say that HTTP/2 improves the user experience and ensures speedier content delivery overall. However, while HTTP/2 is a vast improvement over the original HTTP, it’s still not as secure as HTTPS.
All of these protocols -- HTTP, HTTPS, HTTPS/2, and SPDY -- are not "code;" rather, they are reference models. You can think of them as a set of rules or conventions, as they aren't software. Server implementation can be written in any programming language.
What is HTTP/3?
HTTP/3 will be the first update of HTTP since 2015. HTTP/3, unlike HTTP/2 vs HTTPS, will use a new encryption protocol called QUIC.
QUIC was developed by Google in 2012 for mobile Internet use. Since the first mobile Internet HTTP to HTTPS protocols appeared, the situation and the level of development of information systems have changed, which means that new protocols are required to preserve data confidentiality when transmitting information on the network. Today, mobile devices have become really mobile and people can easily switch from one network to another.
The QUIC protocol uses connectionless User Datagram Protocol (UDP) which works faster than Transmission Control Protocol (TCP).
How to switch from HTTP to HTTPS
How to convert HTTP to HTTPS? There are essential steps that you should make to switch from HTTP to HTTPS:
- Choose the type of SSL certificate you need (some of them used for HTTP vs HTTPS);
- Install SSL certificate to the hosting account;
- Make a total back-up copy of a website;
- Update all links and sitemap from HTTP vs HTTPS;
- Check all templates and references of your site;
- Update javascript, other third-party plugins and robots.txt file and include there your new sitemap;
- Update your Content Delivery Networks SSL settings;
- Turn all landing pages and paid search links to HTTP vs HTTPS protocol;
- Crawl through old URLs to find broken redirect chains and update them;
- Implement 301 redirects to ensure that all users will be redirected to a new HTTPS site;
- Enable HSTS and OCSP stapling.
How to choose SSL certificate
To choose the most suitable SSL certificate for your HTTP vs HTTPS URL, it’s important to understand two aspects: will you collect on your site only names & emails or also private billing information and what kind of services you provide (is your site an information blog, online store or you offer financial services).
There are five types of SSL certificates for HTTP vs HTTPS:
- DV, or Domain Validated - a perfect variant for the sites which don't provide financial functions. To activate will be checked only domain ownership.
- OV, or Organization Validated - is often used by e-commerce websites. Certificate Authority will check all verification documents: identity, website ownership, physical address, and telephone number
- EV, or Extended Validated - offers the highest level of trust for the clients. Such type of SSL is used by popular brands and financial organizations and needs additional verification steps for companies.
- Wildcard - protects all of the first level subdomains of the site (for example: blog.domain.com or mail.domain.com).
- Multi-Domain - use this SSL if you need to protect dates from multiple domains of your site
Conclusion
The important thing to remember is that these protocols have a positive impact in SEO for 2020 and are projected to have a positive impact in 2021 as well. Google and other search engines are really looking closely at page load time and “crawl budget rank,” which make HTTP and HTTPS excellent choices for getting optimal search results.
As you can see, you’ll want to consider your own company’s individual priorities and concerns when weighing your decision on developing your site as HTTPS or HTTP, or other various protocols available. There are a variety of advantages and limitations to each option.
We find that while security is a critical piece of the puzzle, there are more factors to consider when evaluating HTTP and HTTPS than that single issue. We encourage clients to think through all aspects of strategic decisions such as these. However, at the end of the day we currently most frequently recommend going with an HTTPS website protocol. In terms of security, we would rank these common protocols as follows:
- HTTPS
- HTTP/2
- SPDY
- HTTP
If you’d like to learn more about which protocol is best for your company, please contact us at your convenience. We love to talk about HTTP, HTTPS, HTTPS/2, SPDY, and all the other acronyms related to helping your business grow and thrive online.










Comments
It always bugged me why some websites use HTTPS while the rest stays on HTTP. Thanks for the informative article!
Thank you for the thorough explanations! So HTTPS websites are safer for users - good to know. Data safety is vital for everyone today.
I finally found the information I needed. I often heard, but couldn't find information anywhere, not only about the difference between HTTP and HTTPS but also what SPDY and HTTPS/2 are. The article is very useful and informative. Now everything is much clearer. Thank you!
Thank you for this post! I didn't know that SLL is important for SEO
Great article! This is one of the topic I was concerned about and I'm glad that I found this article. I've had a HTTP website for so many years and it didn't occur to me that it's unsecure. Thank you for sharing
Cool! The article is written in simple accessible language about a complex topic. I was finally able to figure out what's what.